InCountry for Analytics
Compliantly maintain global reporting without restricting local operations

Anonymize regulated data for compliant global insights and recombine locally for in-country analytics
It’s increasingly burdensome for data to cross borders, and often a regulatory impossibility. With InCountry, you can anonymize cross-border data flows and maintain both global and local analytics. A global pipeline report doesn’t need to have a prospect’s name and phone number, and a local pipeline report can include all the details for your local staff.
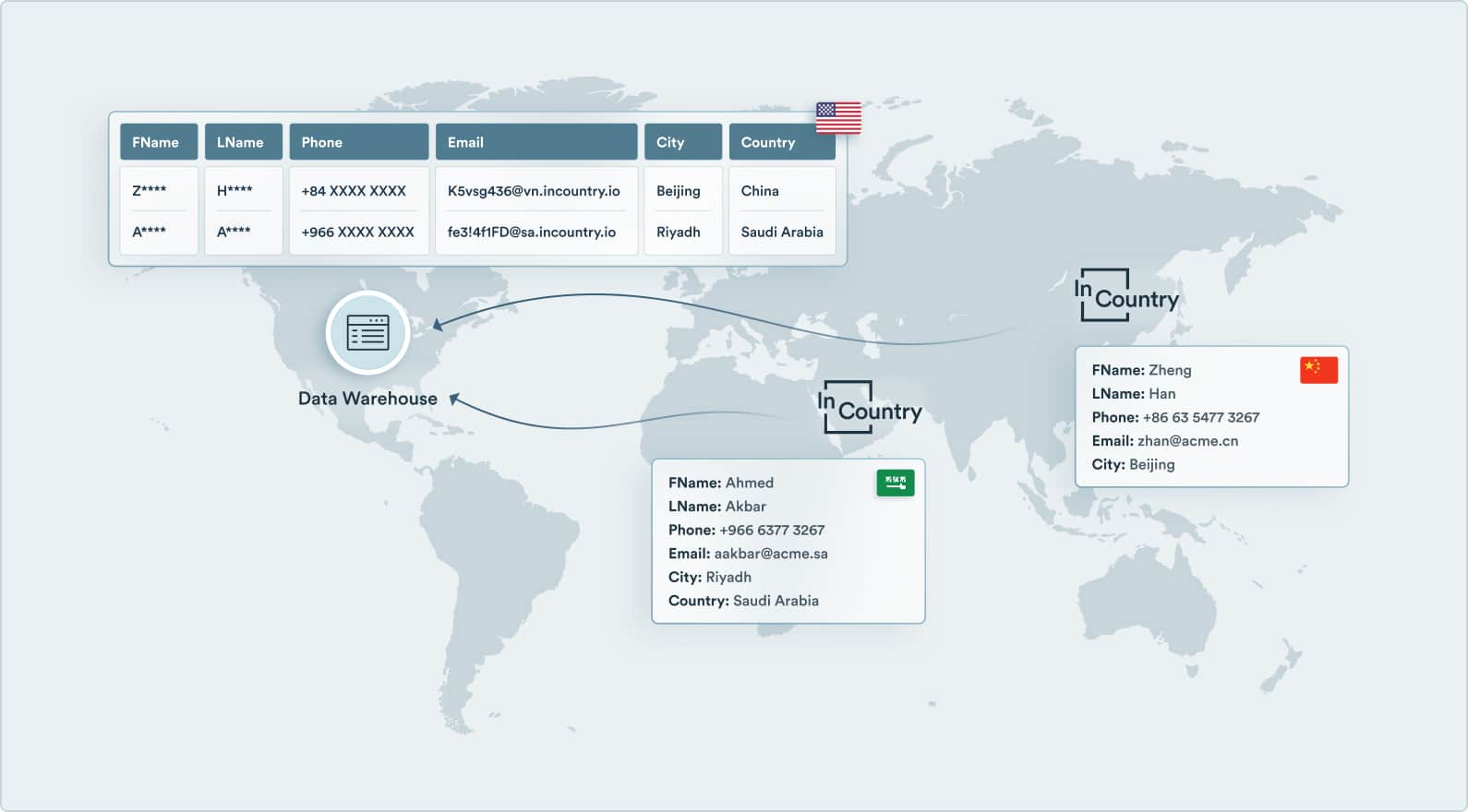
Redact regulated data before it crosses borders and enters the data pipeline
- Integrates with Customer Data Platforms (CDPs) at the source including Salesforce Data Cloud, Segment, mParticle, and Lytics
- Kafka Processor integration redacts and anonymizes PII on the fly
- Message queue guarantees delivery across unreliable networks
- Pre and post process data payloads as they transit the InCountry point-of-presence
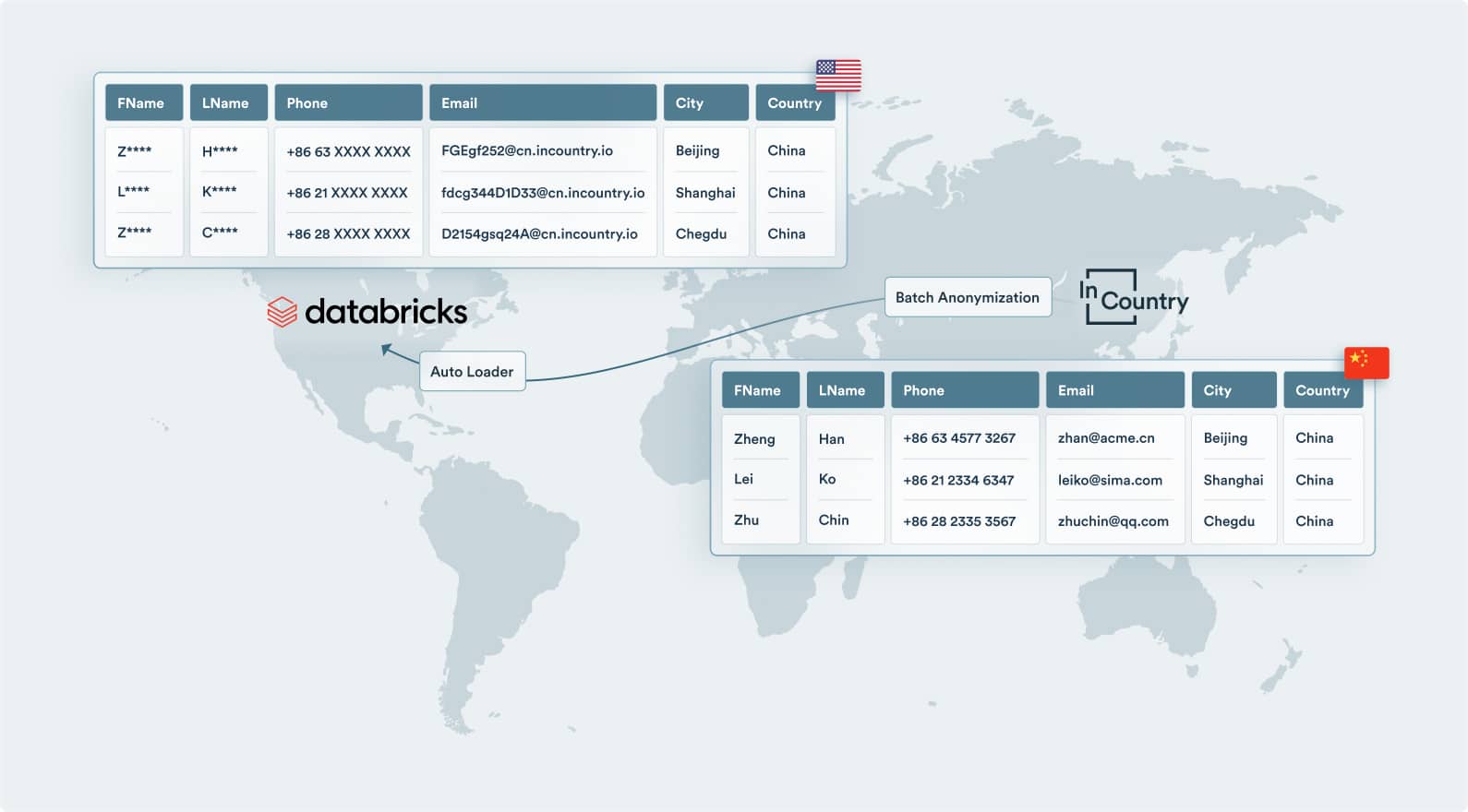
Integrates with batch loading to anonymize regulated data prior to crossing borders
- Operate a global data warehouse or data lake without compromising regulated data
- Redact and anonymize regulated data as part of the transformation step in ETL tools including Mulesoft, Pentaho, and Informatica
- Integrates as a preprocessor prior to crossing borders and sending to bulk data loading mechanisms for Databricks, Snowflake, Teradata, BigQuery, and more
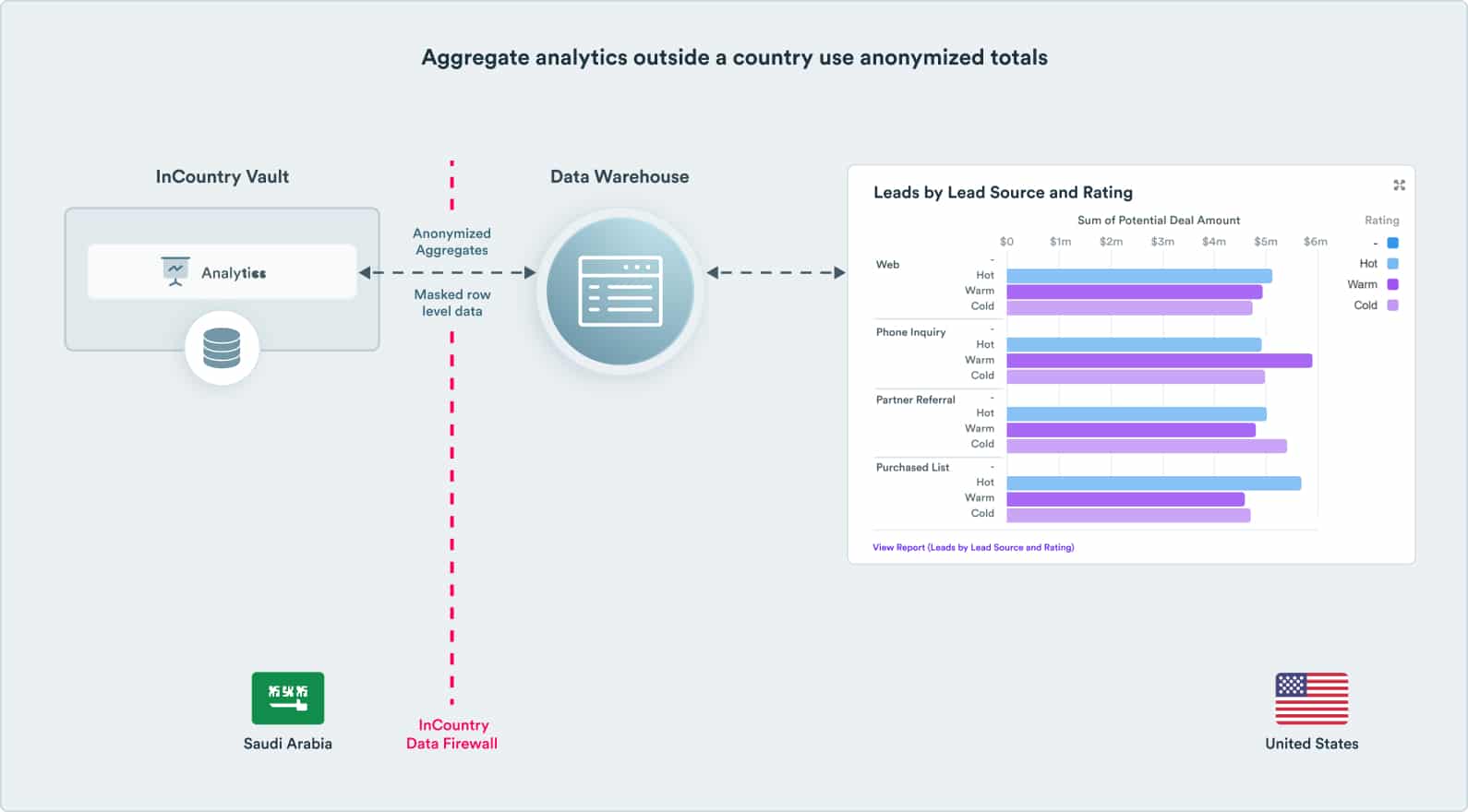
Maintain global analytics with anonymized data
- Anonymize regulated data before it crosses borders and enters the data pipeline
- Business intelligence and reporting tools continue to operate with regulated data fully masked
- Dashboards can directly query local in-country data sources for real-time aggregated numbers
The turnkey, enterprise-grade solution for data residency
Enterprise Ready
- Two points-of-presence in each country with active-active failover
- SaaS, single-tenant anywhere, AWS Outposts, and sovereign cloud options
- Guaranteed messaging across unpredictable networks
Developer Friendly
- Automatically makes forms data residency aware
- Support for Reports, Service Console, attachments, APEX SDK
- Flexible tokenization, hashing, and masking algorithms
Bank-Grade Security
- Policy-based authorization and fine-grained authorization from apps
- Secure SDLC and operations with active threat monitoring
- Searchable encryption using NIST standards
Global Compliance
- Data loss prevention across borders with data firewall and AI PII detection
- Detailed support for regulatory approval in complex jurisdictions
- Downloadable audit logs track every event

