As companies navigate the ever changing political landscape, data sovereignty has grown into an important topic – especially for companies looking to transition to the cloud. This topic is not going away any time soon.
Data sovereignty focuses on the idea that data “home.” And this implies that data is subject to the laws and governance structures that are in charge of the territory where the data was collected.
This new trend that has come into action with the rise of cloud computing means that many countries have passed laws to regulate and control data storage and transfers. Such regulations reflect measures of data sovereignty. As of now, over 100 countries have some sort of data sovereignty laws in action.
Data requirements used to be easy to navigate – in the days of on-premises computing. This was when data was stored in data centers owned by companies locally. Cloud data, on the contrary, is stored in different places and accessed across borders, which forces companies to pay close attention to how they are managing their data in different geographies.
As SaaS, cloud and hosted services are being adopted more rapidly then ever, it is hard to ignore data sovereignty issues. Nevertheless, some organizations assumed that data sovereignty would not affect their business, but this is where they have miscalculated.
Why data sovereignty is important?
Data sovereignty is becoming more of a challenge for businesses once they’re moving to the cloud. In Europe, organizations can be fined up to €20 million if they break the General Data Protection Regulation (GDPR).
GDPR applies not only to EU countries, but to companies that receive data from organizations or people living in the EU. This law has imposed major restrictions for organizations that conduct international business and are executing a cloud-first approach.
What’s more important, some countries have their own data sovereignty laws are difficult to decode and even harder to obey. For example, Egypt’s new Law on the Protection of Personal Data (October 2020) does not imply data localization obligation towards cross border data transfers, but the law does require a license for such transfer of data. The general rule is that data must be transferred to a jurisdiction that offers an equivalent level of cloud data protection to that provided under Egyptian law.
What is data sovereignty in the cloud?
Renewed attention is being directed to issues that arise globally from the storage of business and personal data in the cloud.
Besides existing requirements to keep certain types of data within the country of origin, some nations’ data sovereignty laws introduce significant limitations on data transmission outside the country of origin.
Some countries also have privacy laws that limit the disclosure of personal information to third parties. This means that companies doing business in such countries may be prohibited from transferring data to a third-party cloud provider for processing or storage.
Cloud data can be subject to more than one nation’s laws. Depending on where it is being hosted or by whom it is controlled, different legal obligations regarding privacy, data security and breach notification may be applicable.
In some cases, large categories of data may not be allowed to be transmitted beyond the country’s geographic borders or outside its jurisdiction. Such restrictions affect businesses that employ hybrid cloud strategy – they use multiple cloud providers that maintain local data centers and comply with the separate, local legal requirements for each country.
Despite the benefits of flexibility, scalability and cost savings that offered by cloud infrastructure, companies adopting cloud need to consider potential security and data sovereignty issues.
Most common questions about cloud data sovereignty:
- What is data sovereignty in the cloud?
- What happens if you ignore data sovereignty in the cloud?
- Does it really matter where data is stored, or by whom?
- How can cloud services be used safely and when can they be dangerous?
In this way, companies using cloud infrastructure need to address data sovereignty analysis not only to the chief information officers. Legal department, information technology security, procurement and risk managers, corporate audit – they all need to be involved into corporate governance and risk management practices.
Getting into compliance – creating data protection strategy
So, what should companies storing data in the public should look after to ensure they are compliant with data sovereignty laws?
If you are considering working with a service provider, be prepared to gather answers to a few key questions. As a company, you should understand how to plan usage and sharing your own data.
You also need to make sure your service provider has systems in place. That will resolve whether the service provider can comply with regulations in countries where your company plans to do business.
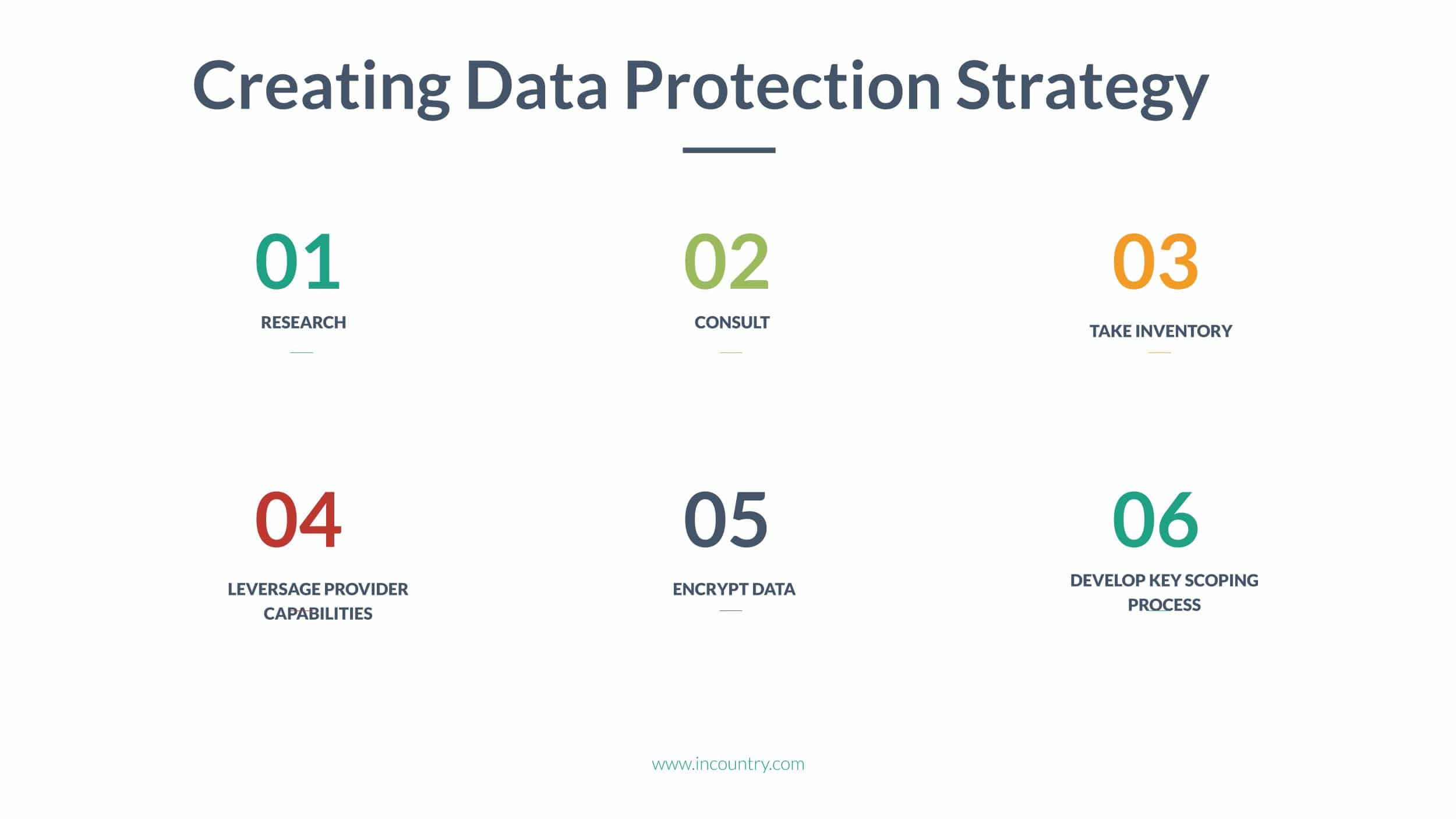
To create data protection strategy which supports your data sovereignty needs, we recommend following these nine steps:
- Understand applicable data residency requirements for your business. Consider them for any location where your company operates or has customers.
- Consult with your legal and/or compliance departments to review legal requirements.
- Take inventory of all cloud data assets and classify them. Identify assets that may contain compliant data from highly restrictive countries.
- Leverage service provider capabilities based on the list of your restricted data locations.
- Encrypt your data. Service providers will have keys and other tools to perform base-level encryption. Check to determine if a specific country requires stricter practices with certain kinds of data.
- Develop key scoping process. You can determine that you need a key that protects specific data assets or data that might touch certain geography. That will give you the ability to customize rules to protect data specific to a particular country.
- Develop compliance monitoring plan. If your data leaves the region, you have the ability to monitor when it leaves, so you can manage it and ensure that it stays in compliance.
Your team must understand what tools and capabilities are available from your cloud service provider. Developing a structured approach to data protection that includes classification, tagging, encryption and monitoring, will make it easier to address your data sovereignty needs. Ongoing carefulness about which regulations apply to your customer base and operating environment is essential.
Multi-cloud architecture and sovereignty issues
What does a typical multi-cloud architecture consist of? It can be two or more public clouds and potentially additional private clouds. This multi-cloud environment helps eliminate dependence on a single cloud provider.
Also, in a multi-cloud environment, synchronization between different vendors is not crucial to complete computation process. But in order to manage data orchestration the company must stipulate storage locations.
Because of sovereignty issues, your multi-cloud architecture can be at risk of violation of multiple nations’ data sovereignty regulations. Specifically because running your applications and services with data centers scattered across geographies means some data center locations can be under strict sovereignty laws. That’s why you need to carefully choose your cloud vendor.
How to select a prospective cloud vendor

Why InCountry is your ideal partner for solving cloud data sovereignty challenges
SaaS cloud solutions can be a great cost-saving solution for many companies, but, depending on your data retention regulatory requirements, may fall short, putting you at risk. Remember, not all clouds are created equally.
Unlike other cloud sovereignty solutions for SaaS, partnership with InCountry will become your fastest way to comply with data residency regulations and unlock new territories.
With InCountry you will:
- Use our platform to localize cloud data – without repeatedly building your full-stack.
- Enter new markets and win more customers – and therefore create new revenue streams from scaling internationally.
- Comply easily with ever-changing data sovereignty regulations in 90+ countries.
- Spend less time on infrastructure and software and have more time to focus on core customer and product experiences.
Frequently asked questions about InCountry
Which compliance and security audits has InCountry undergone?
Information Security is not just a buzzword for InCountry – it‘s our daily work, our passion and the principle that drives us. InCountry is SOC 2 Type II audited and will be certified against internationally-recognized standards such as ISO 27001 for Information Security.
Globally, InCountry is compliant with local data regulations in operational countries. Now InCountry also complies with Federal Law No. 152 “On Personal Data” and is FX-152 compliant.
In what countries is InCountry operates?
InCountry’s platform operates in 90+ countries.
What physical data center security do you provide?
We ensure all data center facilities we use are of at least the Tier III level and are at the minimum certified with ISO27001 or SOC2. The InCountry platform can also be deployed on the data center host provider of choice.
What type of encryption do you use?
InCountry uses SHA-256 for hashes and AES-256 for data payloads.
Does InCountry work with a third-party key management system?
Yes, InCountry integrates with third-party enterprise key management solutions (KMS) provided by third-party vendors and supports bring-your-own-key(BYOK) scenarios.
Who owns the data? How will the data be handled in case of contract termination?
The customer owns their data. In the case of contract termination, InCountry will retain the customer data as agreed in the contract for data retrieval purposes or migration.
Ready to take the next step with data sovereignty?
Right now, companies are facing the challenge of navigating through the rules that individual countries develop to ensure their own citizens’ data is being protected.
There are no universal, global standards around data sovereignty on the horizon, and “splinternet” is the new trend. Although a unified set of rules across all countries would simplify moving to the cloud, most nations have their own interests.
InCountry is here to help you solve data sovereignty issues quickly and efficiently.